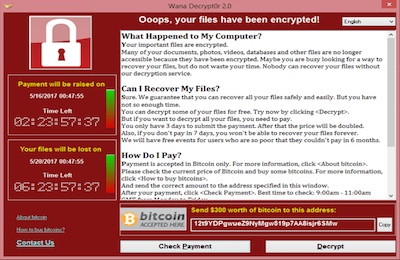
Ransomware Word For Mac
They are using email addresses and subjects that will scare or entice a user to read the email and open the attachment. A very high proportion are being targeted at small and medium size businesses, with the hope of getting a better response than they do from consumers. You or your email provider have not been hacked or had their email or other servers compromised. They are not sending the emails to you. They are just innocent victims in exactly the same way as every recipient of these emails. The email looks like: From: random name at your own domain Date: Tue 09:50 Subject: FW: Documents Requested Attachment: Untitled(1).docm Body content: Dear [ your name ], Please find attached documents as requested.
Apr 10, 2015 - Ransomware attackers have resorted to reviving a very old attack vector, the malicious Word macro. I manually created a few files on the computer using Microsoft Word, PowerPoint, and Notepad, because ransomware is known to target file extensions for the most commonly used files to inflict the. Video editors with selective coloring for mac free.
Best Regards, Lizzie Screenshot: 9 August 2016: Untitled(1).docm: show a download of the encrypted Locky/zepto binary from www.fliegendergaertner.at/09uh8ny which gets converted to a working.exe file by the malicious macro in the original word doc. To give zorgins.exe ( ) Previous campaigns over the last few weeks have delivered numerous different download sites and malware versions. There are frequently 5 or 6 and even up to 150 download locations on some days, sometimes delivering the exactly same malware from all locations and sometimes slightly different malware versions. Dridex /Locky does update at frequent intervals during the day, sometimes as quickly as every hour, so you might get a different version of these nasty Ransomware or Banking password stealer Trojans. All the alleged senders, companies, names of employees, phone numbers, amounts, reference numbers etc. Mentioned in the emails are all innocent and are just picked at random. Some of these companies will exist and some won’t.
Don’t try to respond by phone or email, all you will do is end up with an innocent person or company who have had their details spoofed and picked at random from a long list that the bad guys have previously found. The bad guys choose companies, Government departments and other organisations with subjects that are designed to entice you or alarm you into blindly opening the attachment or clicking the link in the email to see what is happening. This email attachment contains what appears to be a genuine word doc or Excel XLS spreadsheet with either a macro script or an embedded OLE object that when run will infect you.
Modern versions of Microsoft office, that is Office 2010, 2013, 2016 and Office 365 should be automatically set to higher security to protect you. By default is enabled and macros are disabled, UNLESS you or your company have enabled them.
If mode is turned off and macros are enabled then opening this malicious word document will infect you, and simply previewing it in windows explorer or your email client might well be enough to infect you. Definitely DO NOT follow the advice they give to enable macros or enable editing to see the content. Most of these malicious word documents either appear to be totally blank or look something like these images when opened in mode, which should be the default in Office 2010, 2013, 2016 and 365. Some versions pretend to have a digital RSA key and say you need to enable editing and Macros to see the content. Do NOT enable Macros or editing under any circumstances. At this time, these malicious macros only infect windows computers. They do not affect a Mac, IPhone, IPad, Blackberry, Windows phone or Android phone.